Getting WordPress Brute Force Login Attacks Down to Zero
I was always mildly concerned of the brute force logon attempts to my blog. Using plugins, I renamed the login page and disabled the XML-RPC API calls that require login. As a result, I was able to bring attacks down to zero.
The Details (This is a Short One)
As many WordPress bloggers, I use the Limit Logon Attempts Reloaded plugin (LLA) as a countermeasure to brute force attacks on the login page. Ever once in a while I looked into the logs, which did not really make me nervous, because A) numbers usually stayed well below 200ish attempts per day, and B) the names the attackers tried were far off the mark. Still, it was always nagging me, and recently I had this brilliant idea: Why not rename the login page? Turns out, I was absolutely not the first to get to this – admittedly rather obvious – idea. There are even plugins ready made for that – so many actually, that it is difficult to choose one. I ended up with WPS Hide Login, mainly for it being free, having tons of 5-star reviews and massive installation numbers.
But surprise: Failed and blocked login attemps did go down, but not down to zero – huh? A quick glance at the LLA logs identified the culprit – XML RPC:
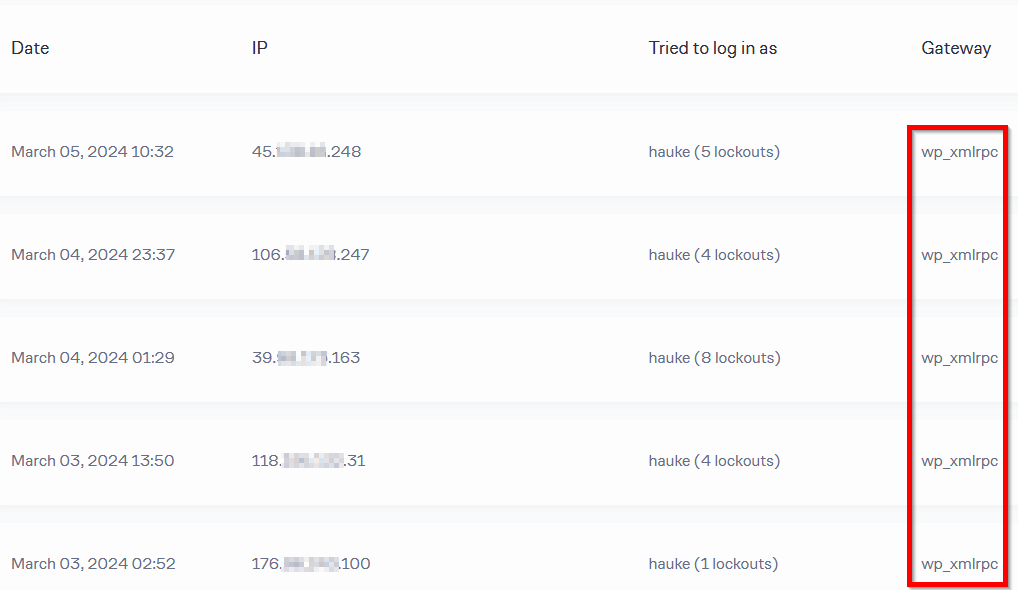
This API exposes endpoints that require authentication. Guess what: There’s a plugin to switch that off also. And since I did not need it, that’s what I did, using Disable XML-RPC by Phil Erb. Selection criterion here was simplicity: Most plugins that offer the functionality, overdo it, by using the builtin WordPress filter (which is what Phil’s plugin does), plus .htaccess modifications, plus also disabling the JSON API, plus, plus, plus – all things I was not interested in. Phil’s plugin just adds the one required filter line in a compatible and stable way – nothing else needed.
And now I’m down to zero:
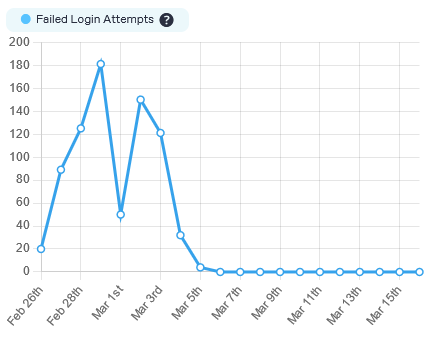
Big thanks to the providers of the plugins – highly appreciated!
